Not Your Keys, Not Your Coins
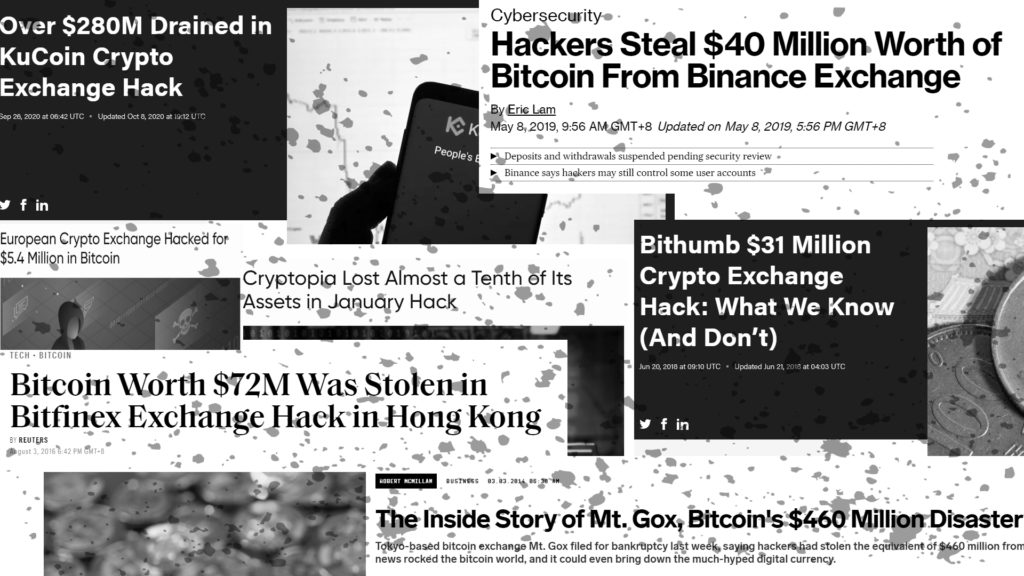
Since the inception of Bitcoin and the cryptocurrency industry, there have been approximately 50+ exchanges hacked, with more than $2 billion in stolen money from exchange users.
Unfortunately, since Bitcoin and most cryptocurrencies are pseudonymous, hackers can potentially get away with hacking these exchanges, running away with huge amounts of money from the exchanges’ users with them.
The only way to combat this issue is to use reputable non-custodial wallets and to learn how to protect yourself from hackers and scammers.
Non-custodial wallets are wallets whereas your wallet’s recovery seed isn’t stored on any company’s servers. Instead, the recovery seed is only stored safely and encrypted locally on your device.
What’s a recovery seed?
A wallet’s recovery seed is a string of 12-24 words that’s mostly provided when generating a new wallet. This string of 12-24 words can then be used to restore your wallet to other devices.
A recovery seed is also mostly referred by people as “backup seed”, “recovery phrase”, “backup phrase”, etc.
Hence, with a non-custodial wallet:
- You have full self custody over your funds, and nobody would be able to freeze or take control over your funds.
- Your funds are totally safe from the inevitable security breaches of exchanges, and custodial wallets.
- You’re not required to submit AML/KYC documents.
- You have better privacy in general.
What’s AML/KYC?
AML stands for “Anti money laundering”, while KYC stands for “Know your customer”.
If a certain exchange or service in general requires AML/KYC, it means that they will require you to submit personal identification documents for you to be able to use their platform.
Some Non-Custodial Wallets
- Hardware: Ledger Nano X | Trezor Model T
- Mobile: BlueWallet | BRD
- Desktop: BlueWallet | MetaMask
Out of the bunch, hardware wallets provide the best security. Due to the fact that even if your computer or smartphone gets infected by malware, your funds will still be safe as long as you only store your backups physically not digitally.
Though the security of your phone compared to your computer completely depends on their operating systems and how you use them, smartphones tend to mostly be more secure than computers.
When having a wallet on your phone or computer, make sure to prevent downloading unnecessary files, and installing unnecessary programs.
Basic Beginner Security Guidelines
- Install the uBlock Origin(Chrome, Firefox) ad blocker plugin on your browsers, to prevent you from accidentally clicking on scam advertisements.
- Exchanges get hacked all the time. If you don’t trade, withdraw your funds to your own non-custodial wallet.
- Make sure you’re downloading wallet software from their official websites or their official App Store/Google Play pages.
- Do not store your wallet’s recovery seed digitally. Write it down, or get yourself a metal backup storage.
- Protect your wallet’s recovery seed. Once someone gets ahold of your recovery seed, he/she gets full control over your funds.
- Do not enter your wallet’s recovery seed anywhere, besides when restoring your wallet to another device.
- Before sending your funds from your exchange to your non-custodial wallet, make sure to test your recovery seed first. Just to be extra sure.
- Don’t flaunt your holdings, as to prevent $5 wrench attacks.
- As much as possible, avoid exchanges that require AML/KYC. Use peer-to-peer exchanges like HodlHodl, LocalCryptos, and Bisq instead.
- Educate yourself about cryptocurrency scams.
Learn more about Security
- In-depth Guide to Bitcoin Wallets
- Security vs. Complexity
- The Dos and Don’ts of Bitcoin Key Management
- Documented Timeline of Exchange Hacks
- Documented Physical Attacks
- Crypto Scam Database
- The Cryptocurrency Scambook
Learn more about Privacy
- Protect your privacy – Bitcoin.org
- What is CoinJoin?
- A Technical Overview of Wasabi Wallet, Future Ideas, Plans and Strategy
- no-KYC only – Avoid the creep
- Coin Control Is Must Learn If You Care About Your Privacy In Bitcoin
- Securing Your Financial Sovereignty
“There are only two types of companies: those that have been hacked, and those that will be.“
– Robert Mueller, Former FBI Director